Vulnerability Mapping
Week 6 (6 April 2018)
1.0 Port Scanning Definition
There are 3 types of vulnerabilities, Design vulnerability due to the weakness in software specification, Implementation vulnerability which can be found in the security glitches in the code, and Operational Vulnerability is where there is an error in deployment.
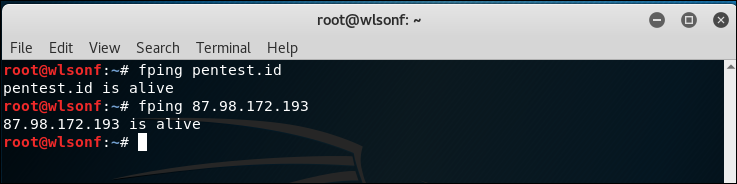
Just like the previous post, to scan port, we will learn more about mapping by using Hping and Fping and other tools. Fping is to ping multiple IP addresses simultaneously while Hping is use to manipulate and listen to IP packets.
2.0 Tools
2.1 FPing
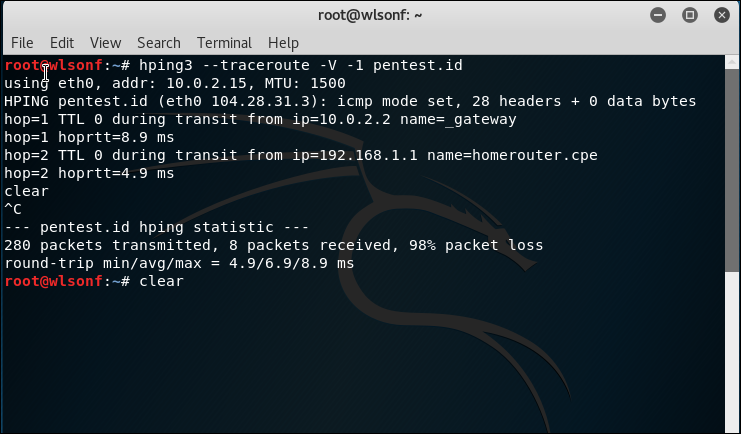
2.2 HPing
Hping cheat sheet can be found here. More example can be found here.
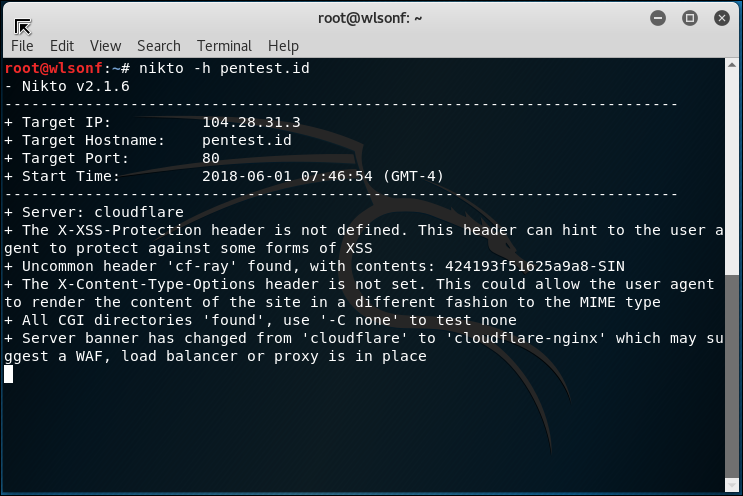
2.3 Nikto
Nikto can be use to find the subdomain and the directory aswell.