Utilizing Search Engine
Week 3 (9 March 2018)
5.0 Utilizing The Search Engine
In Continuation of the previous post(week), hacking can also be done by using search engine, we can use certain keywords / query to find anything that is left behind by sys-admin or web developer.
5.1 Google Hacking
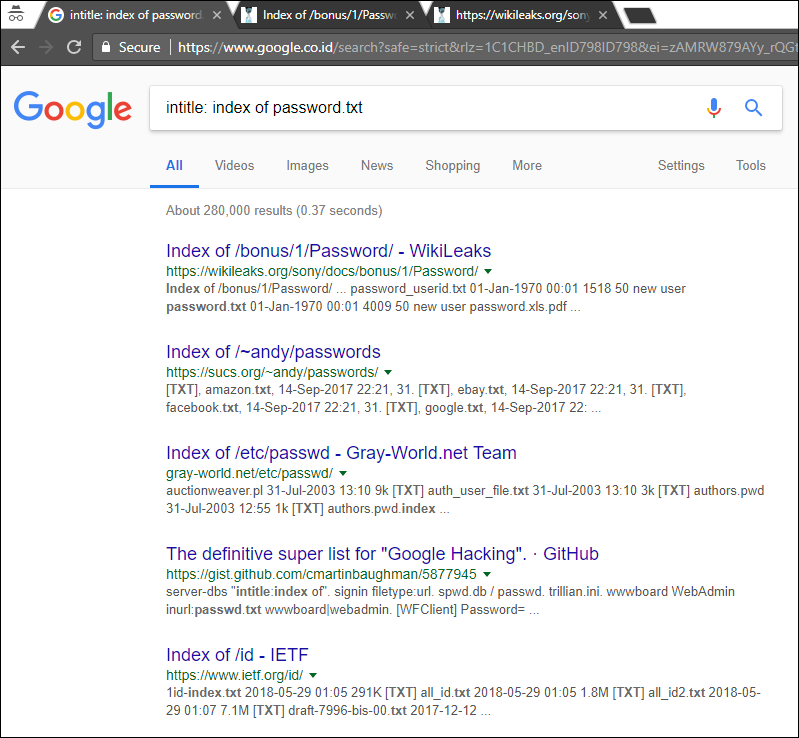
Google hacking can be use to gain sensitive information in google.
intitle:
inurl:
intext:
define:
site:
phonebook:
maps:
book:
info:
movie:
weather:
related:
link:
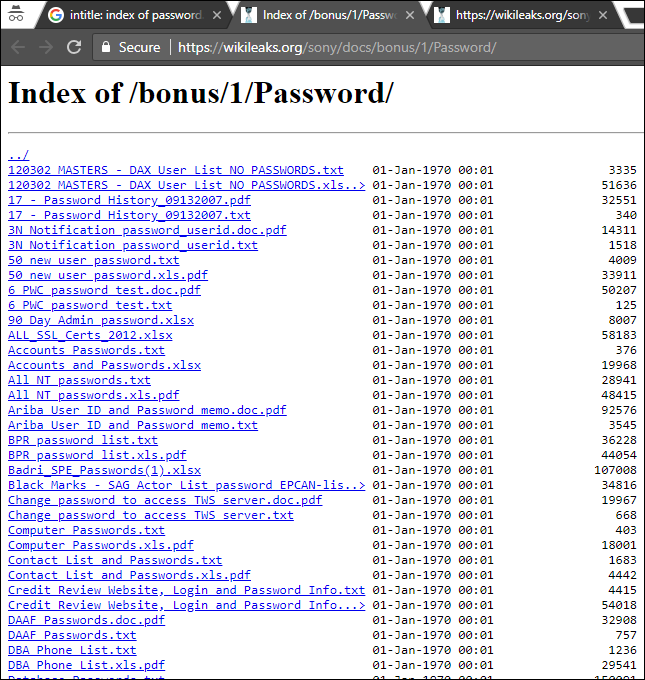
Below is the example how to use google hacking, it’s only recommended that you use it to find your own website.
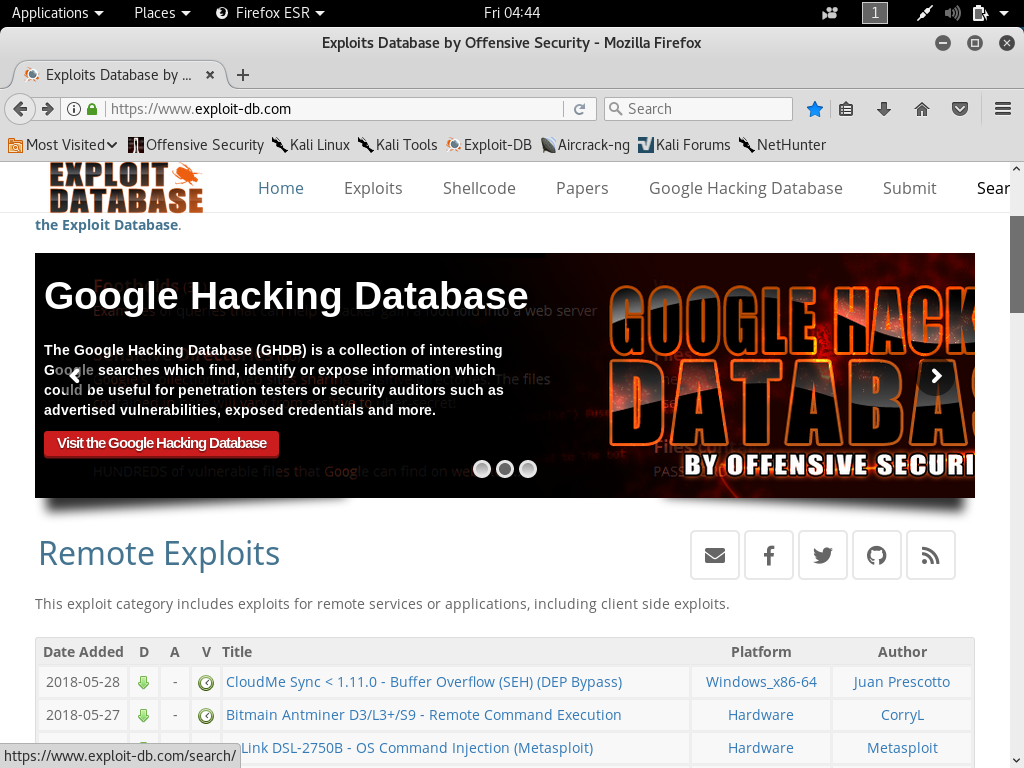
5.1.1 Database Exploitation
Db Exploit is used to finds specific exploitation in database from somewhere, exploit-db can easily be found in kali linux firefox’s bookmark tab.
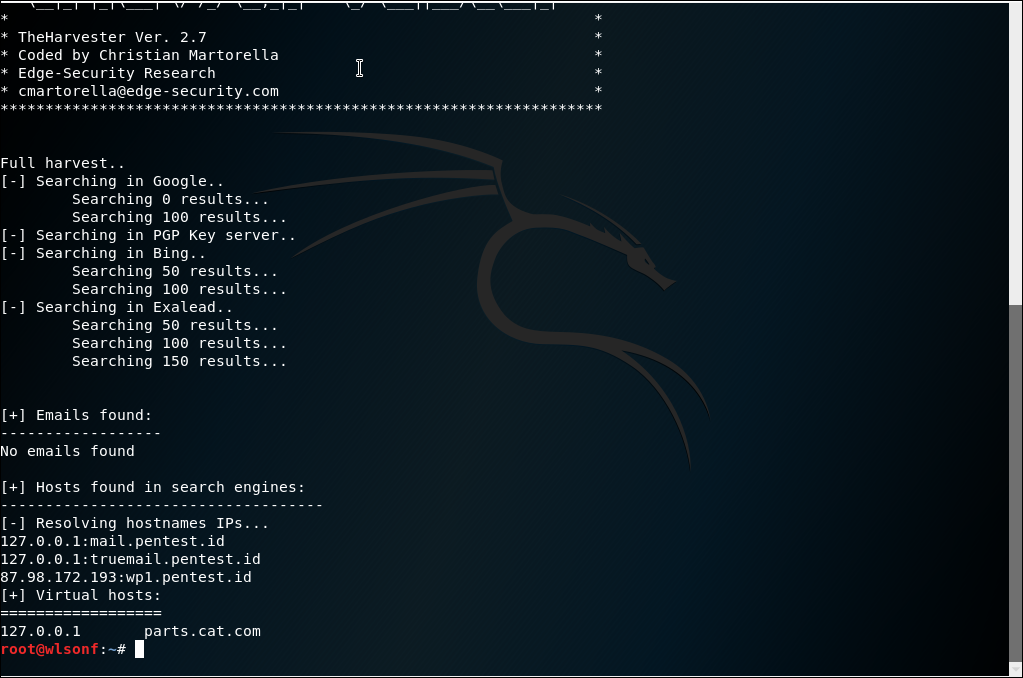
5.2 Theharvester
The harvester is a tool to collect email, username, name, etc from the internet, the command used is ~# theharvester -d domainname -b all
All means that the tool will look onto every website (google, pgp, bing). Can also be use to find in social media such as linkedin.